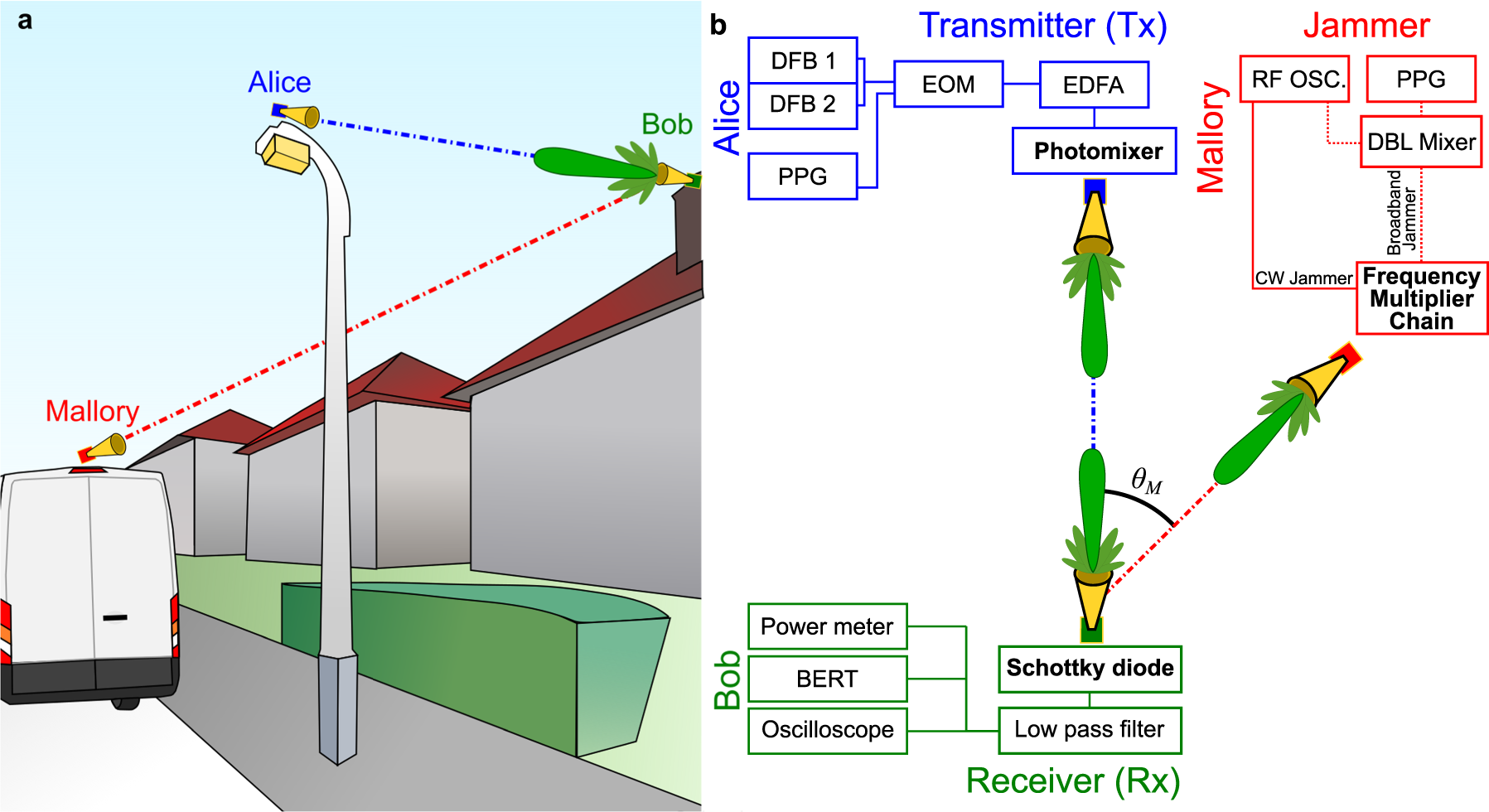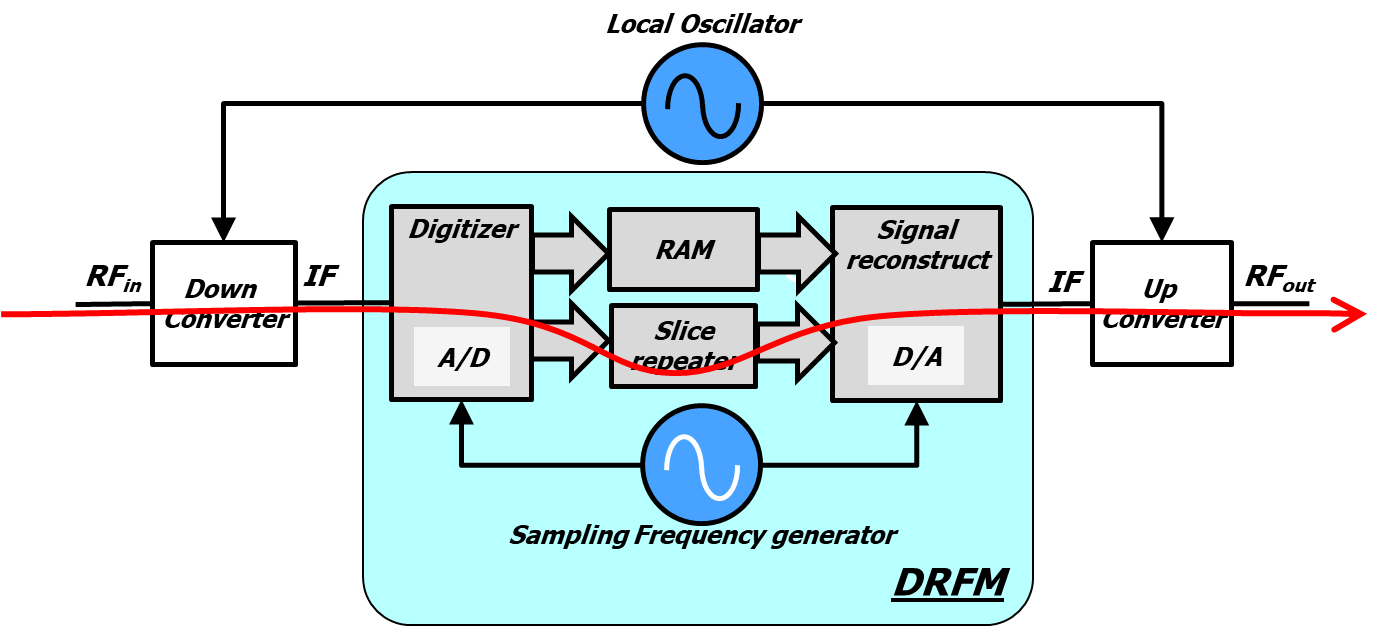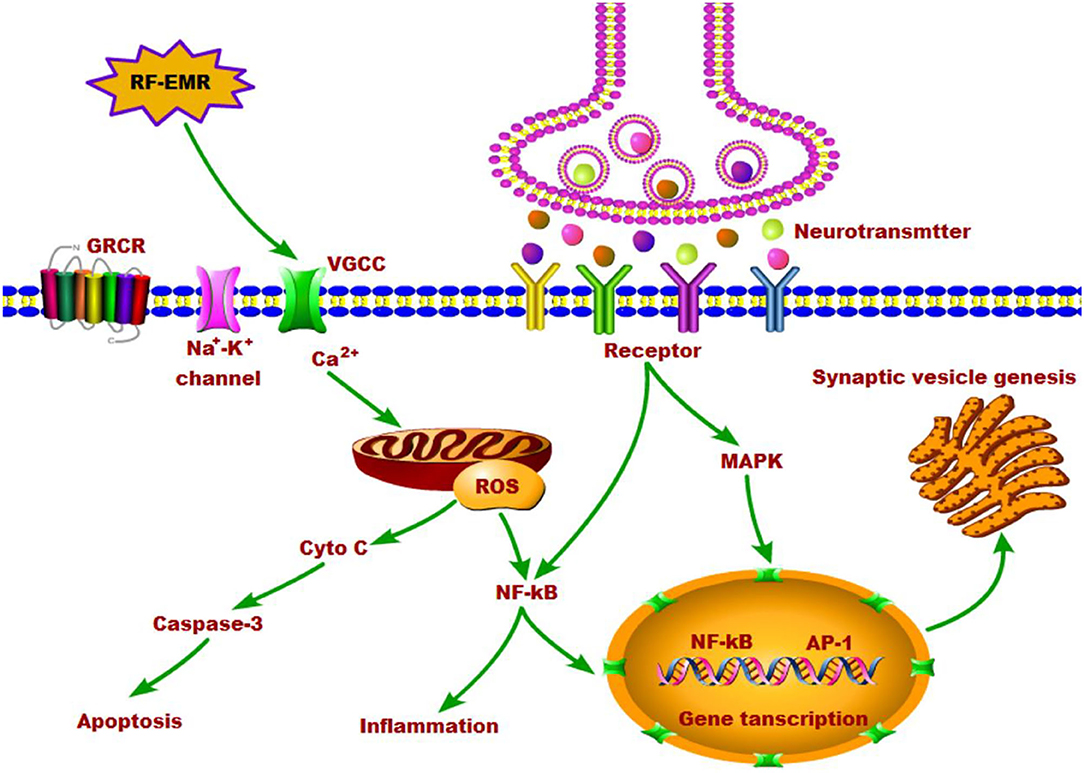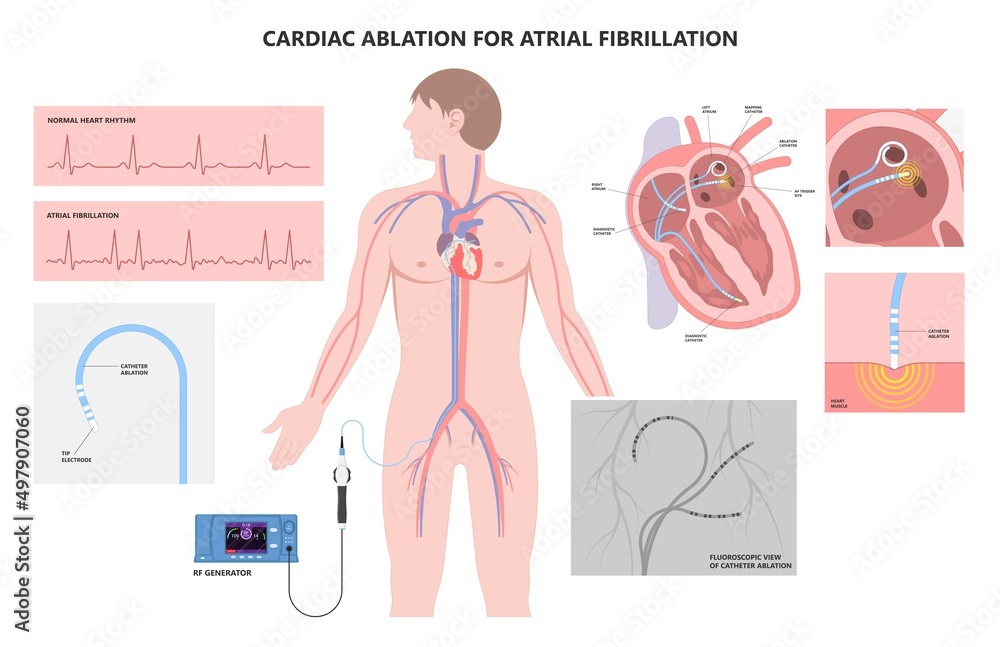
Cardiac catheter ablation treatment Atrial fibrillation rhythm problem minimally invasive procedure attack cath lab treat Coronary x-ray Radio frequency Sinus Ventricular SVT ECG ICD Radiofrequency AV Stock Vector | Adobe Stock

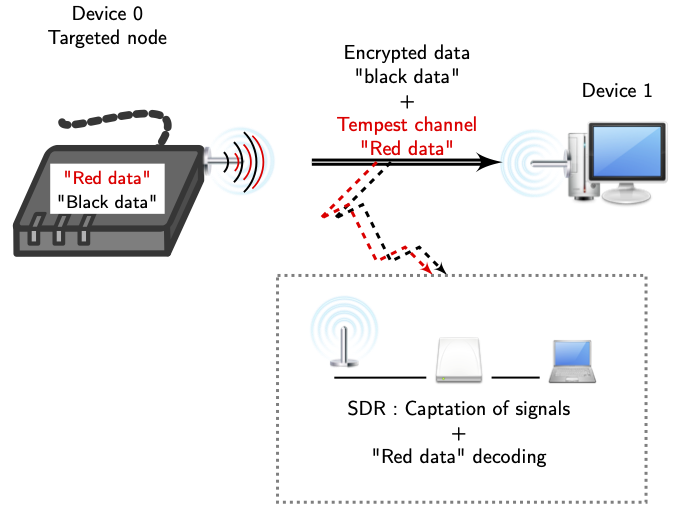
Radio Frequency: An Airbone Threat to Corporate and Government Networks | 2020-07-06 | Security Magazine

Radio Frequency: An Airbone Threat to Corporate and Government Networks | 2020-07-06 | Security Magazine

Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News
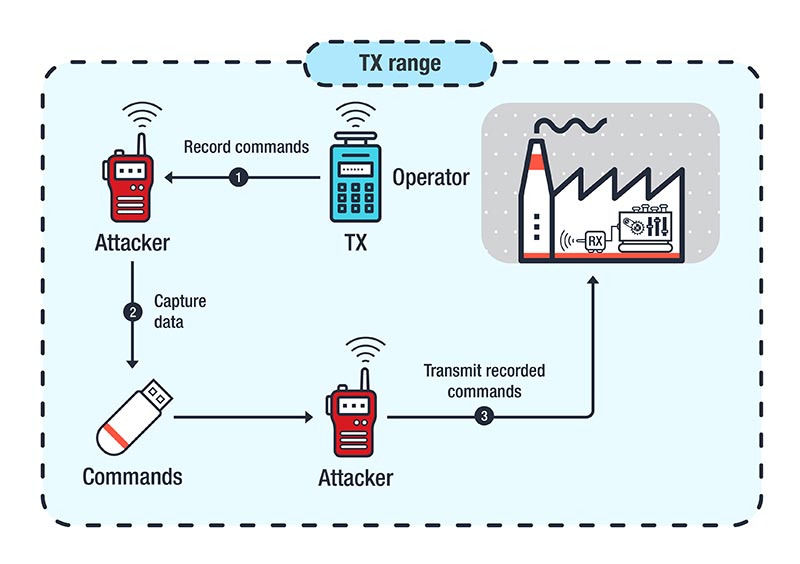
Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News

How to Hack Radio Frequencies: Hijacking FM Radio with a Raspberry Pi & Wire « Null Byte :: WonderHowTo

Microwave weapons that could cause Havana Syndrome exist, experts say | Weapons technology | The Guardian

Applied Sciences | Free Full-Text | Detection of Primary User Emulation Attack Using the Differential Evolution Algorithm in Cognitive Radio Networks